CTF Writeups
Infobahn CTF'25
m0leCon Teaser CTF 2025
Hack the Madness CTF Round 2 (Purdue vs. KSU)
LakeCTF '24-'25 Quals
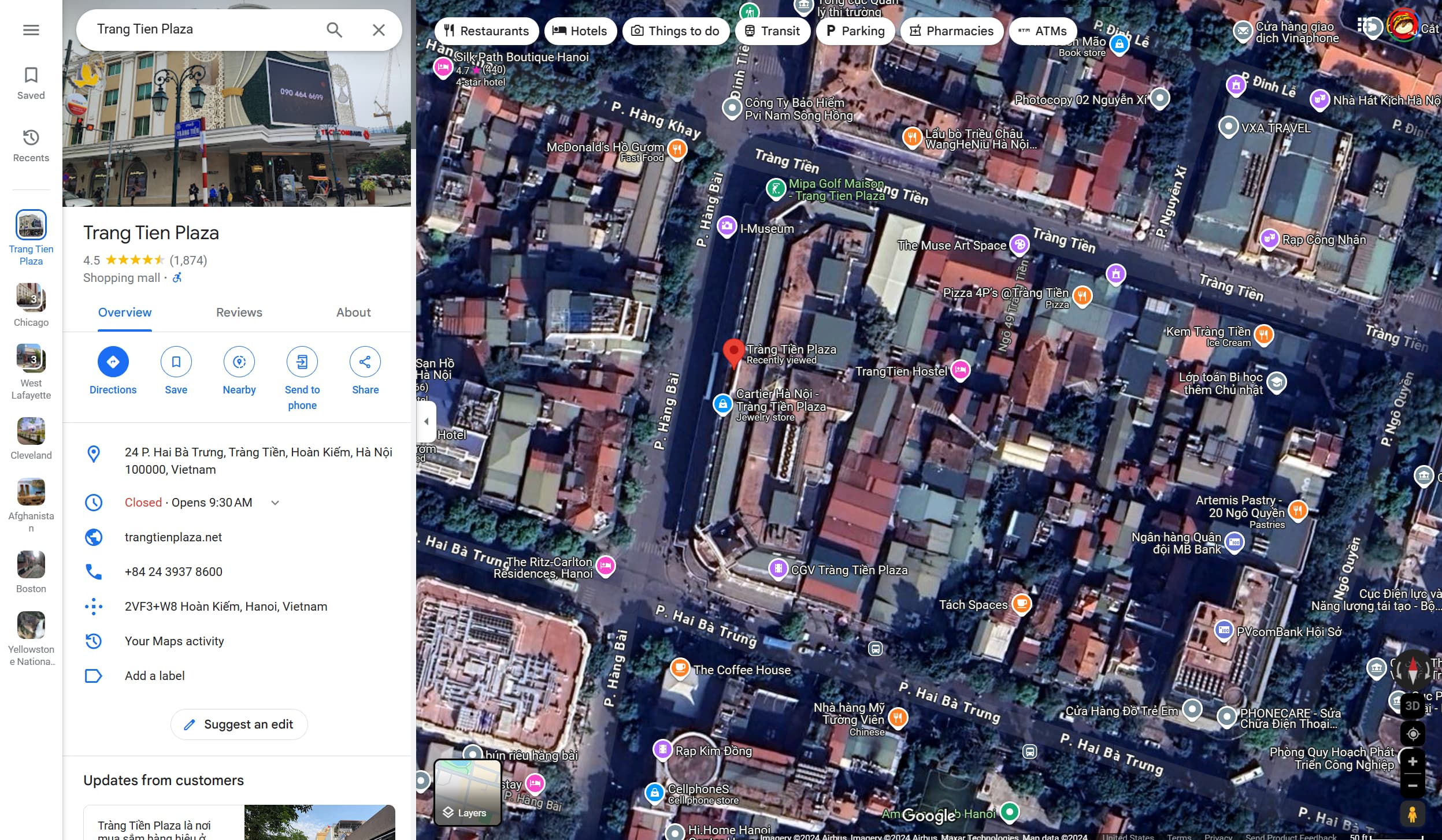
osint/Trackdown
osint> There's a fugitive on the loose and we need to track him down! He posted this to social media recently, do you know where the photograph was taken from? If you can provide the precise building, we can move in immediately 🚔

osint/Trackdown 2
osint> We didn't get him in time 😫 Thankfully, we don't believe he's fled the country yet. He uploaded another photo this morning, it's as if he's taunting us! Anyway, this may be our last chance - do you know where he is right now?
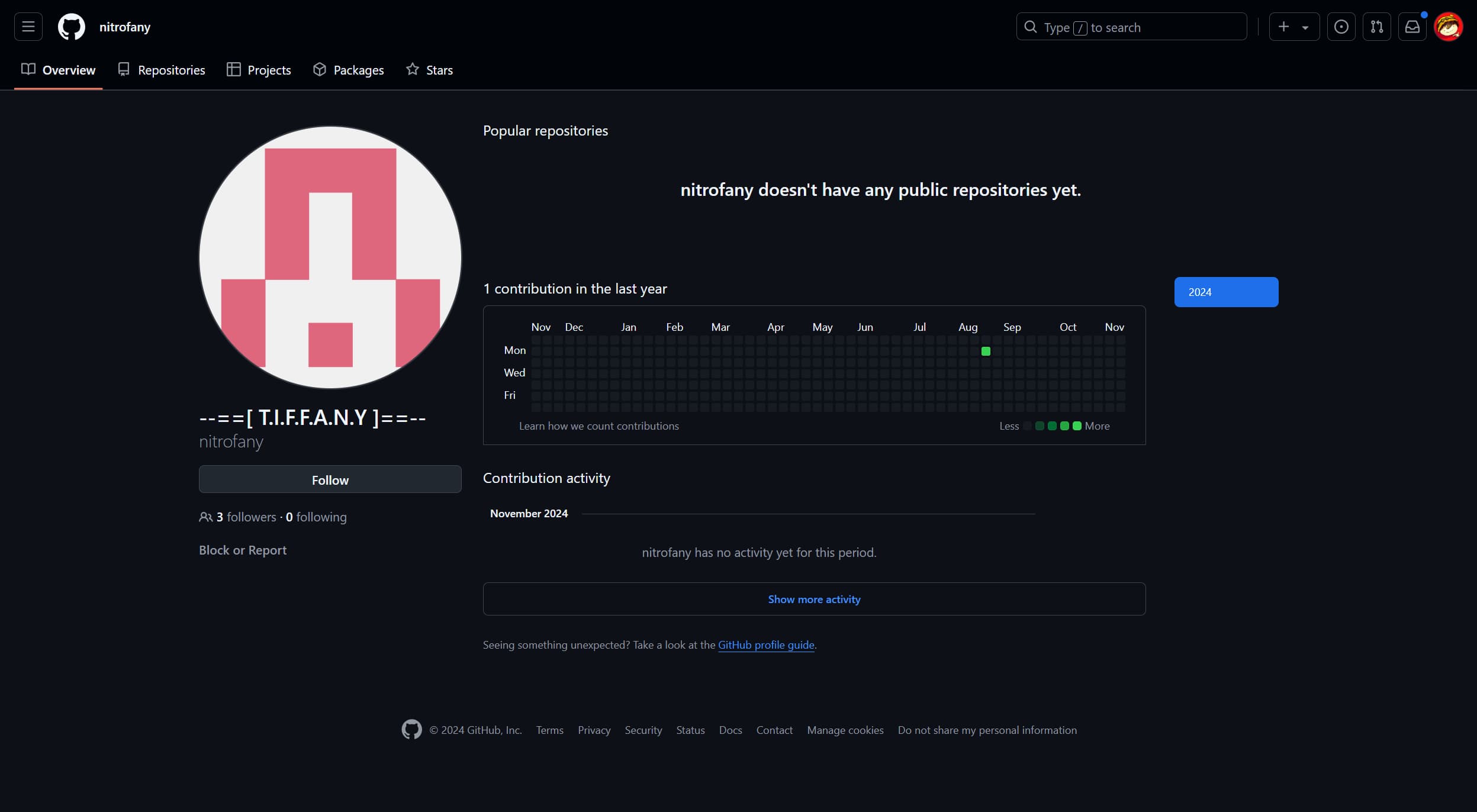
osint/Private Github Repository
osintgithub> Bob Robizillo created a public instructions for Tiffany, so she can start work on new secret project. can you access the secret repository?
1337UP LIVE CTF 2024
BuckeyeCTF 2024
misc/Really Only Echo
misc> Hey, I have made a terminal that only uses echo, can you find the flag?
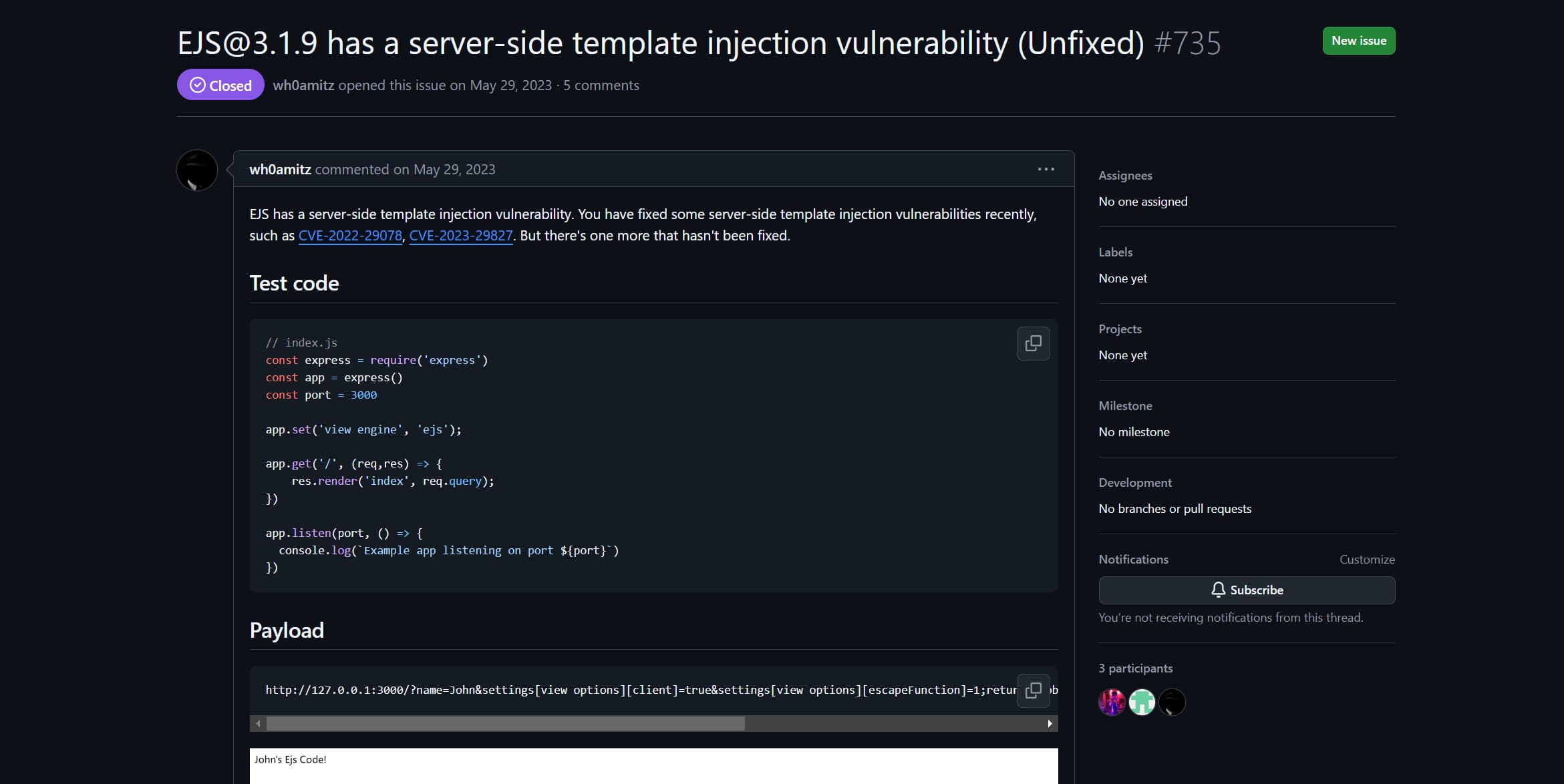
web/Blob
webssti> blob says: blob
misc/Let's Play [steg]Hide & Seek
miscimgproc> Not much of a backstory here... there is an embedded flag in here somewhere, your job is to find it.
PatriotCTF 2024
misc/SKK?
miscimgproc> What have you done to my flag?
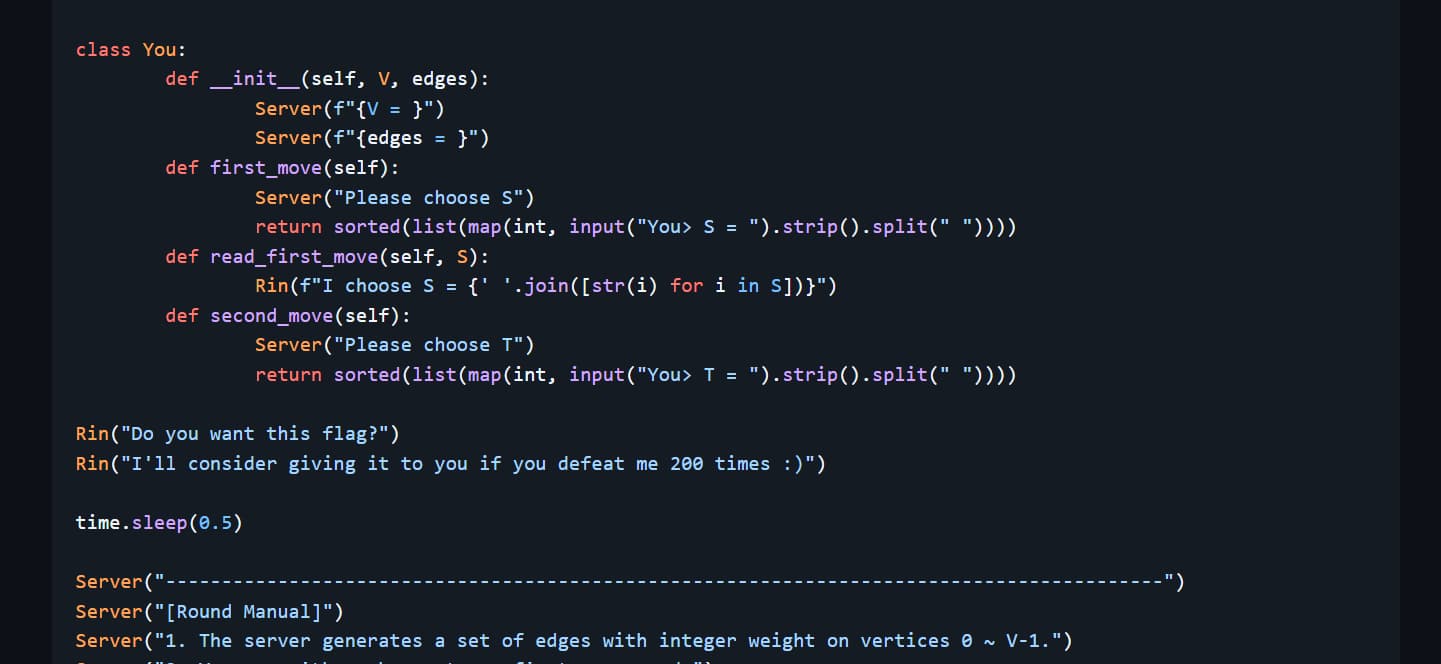
misc/Game with Rin
miscscripting> Nanakura Rin, a very skilled gamer, took one of the flags. You need to defeat her 200 times to get the flag back.
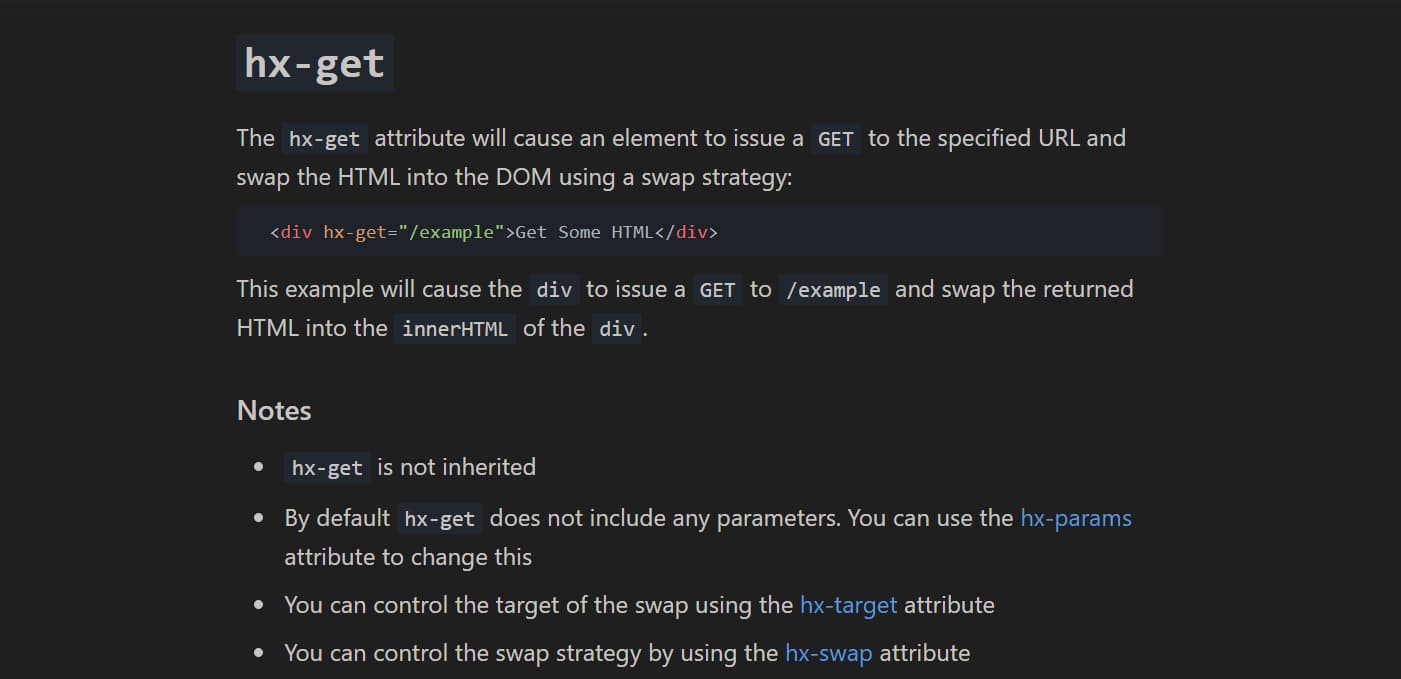
web/trendz(zz)?
webhtmxxss> The latest trendz is all about Go and HTMX, but what could possibly go wrong? A secret post has been hidden deep within the application. Your mission is to uncover it.
CyberSpace CTF 2024
LITCTF 2024
osint/Hip With the Youth
osint> The Long Island Subway Authority (LISA), in an attempt to appeal to the younger generations, has begun experimenting with social media! See if you can find a way to a flag through their Instagram.
osint/An Unlikely Partnership
osint> It appears that the Long Island Subway Authority (LISA) has made a strategic business partnership with a surprise influencer! See if you can figure out who.

osint/The Weakest Link
osint> LISA and the secret business partner have a secret Spotify collaboration planned together. Unfortunately, neither of them have the opsec to keep it private. See if you can figure out what it is!
osint/Night
osint> That was quite a pretty night view, can you find where I took it? Flag format: uiuctf{street name, city name} Example: uiuctf{East Green Street, Champaign}

web/Log Action
webnext> I keep trying to log in, but it's not working :'(
UIUCTF 2024
TJCTF 2024
osint/Chill Beats
osint> Why don’t we all just take a break from hacking and enjoy some music on my webpage? https://0xcafe.neocities.org/
web/calculator
web> I made a calculator! I'm using Python to do the math since I heard it's strongly typed, so my calculator should be pretty safe. Download the source code by clicking the download button above!
crypto/Raccoon Run
cryptorandcrackscripting> The annual UC San Diego Raccoon Run is happening right now!! Apparently there's an underground gambling ring going on there. Maybe you can make it big?
SDCTF 2024
misc/Krusty Katering
miscscripting> Krusty Katering is hemorrhaging money, and Mr. Krabs has brought you in to fix it. You have 10 line cooks, and while they're okay at making Krabby patties, they can't agree on who cooks what and when. To make matters worse, Squidward (trying to keep his job) refuses to give you the list of orders, and will only tell you them one by one. Each time Squidward tells you a job, you get to add it to a cook's schedule for the day. Cooks cannot trade jobs, once it's on the schedule, it stays there. You want to ensure the last order finishes as soon as possible so that Mr. Krabs can close and count his profits. The competing Plankton's Provisions assigns their jobs randomly. So long as your crew is 20% more efficient than Team Chum Bucket every day this week, you're hired. Can you save Mr. Krabs' business?
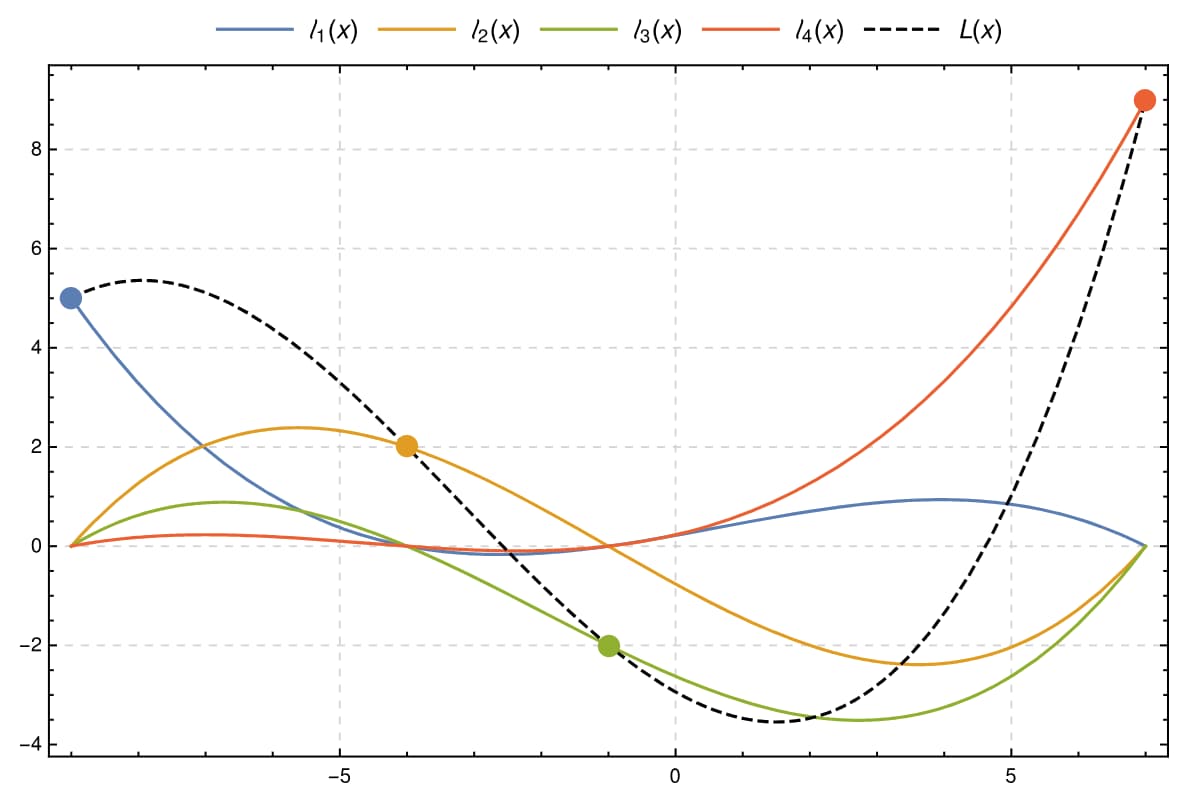
misc/100 degrees
misc> Mr. Krabs has been tinkering with the restaurant thermometer to see what makes his staff the most productive. He's been tracking the data in his journal, but some "Lagrange" guy just called saying Mr. Krabs already has all the info he needs. Can you help Mr. Krabs predict how his staff will fare?
misc/Stop the voices
miscimgproc> Patrick’s been trying to remember the flag, but his vision seems a little blurry and the voices just don't stop...
UMass CTF 2024
misc/gacha
miscimgproc> All my friends have been getting into genshin and honkai recently and keep sending me pictures. However, they keep hiding their favorite characters, demanding for more money for their gacha pulls.

misc/jsfudge
misccharset> JsFudge this JsFudge that, why don't you JsFudge the flag.
misc/my poor git
misc> My poor git server! I think someone took a hammer to the server and ruined a few of the files!
LA CTF 2024
apk/MyVault
apk> Welcome to our secure vault !
osint/Cheater
osint> Our team received a request from a man who believes his wife may be cheating on him. He asked us to help by checking her accounts for any evidence. He provided his wife's name, "Hamdia Eldhkawy" and mentioned that a friend informed him she shared a picture with someone on social media. He couldn't find the image and wants us to discover the man's real name.
0xL4ugh CTF 2024
DiceCTF Quals 2024
escape_from_markov
> We made a fake flag generator just for this CTF! It can generate flags that look like the real one! Can you find the real flag?
IslandParty
imgproc> You open your mailbox and find a strange postcard (invite.bmp). Flipping it around, you squint your eyes and try to decipher the wobbly handwriting:
CI Ninja
prompt engineering> I found this project that uses a state-of-the-art fully automatic patching system. I could not find a way to break it, but I know the flag is in /flag.txt. Do you think you can get it?
Mystical Castle
pddl> In the mystical realm of Eldoria, a land shrouded in legends and whispered secrets, there lived a young adventurer named Alex. With a heart full of curiosity and a spirit as wild as the wind, Alex had always been drawn to the tales of old, the kind that grandparents would recount by the flickering fireside on starless nights. Among these tales, one stood out - the story of the ancient Castle of Shadows, a place where time seemed to stand still, and where every corridor and chamber held a secret waiting to be uncovered.
CI Ninja 2
prompt engineering> Oh no, my exploit does not work anymore! Something's not quite right with these "available functions". Can you help me figure it out?
Stop the model thief!
> To steal an ML model, an attacker often sends 'very similar versions' of the same image, which tells the attacker how the model reacts to very small changes in the input. You realized that an attacker might be trying to steal your image classification model. You're given two files - [1::model_queries.npy] a list of images that your model received as inputs and [2::user_query_indices.txt] a list of image indices (starts from zero) in [1] sent to your model by each user-id. In [2], each line contains the indices from a different user-id (e.g., the very first line is user-id 0, the second line is user-id 1). Can you help us find the attacker's user-ids (there are 20 of them)? Note:: if there were 4 attacker user-ids (e.g., 82,54,13,36), the flag will be 'ictf{13,36,54,82}' (sorted, no quotes).
iCTF 2023